Orchestra Central
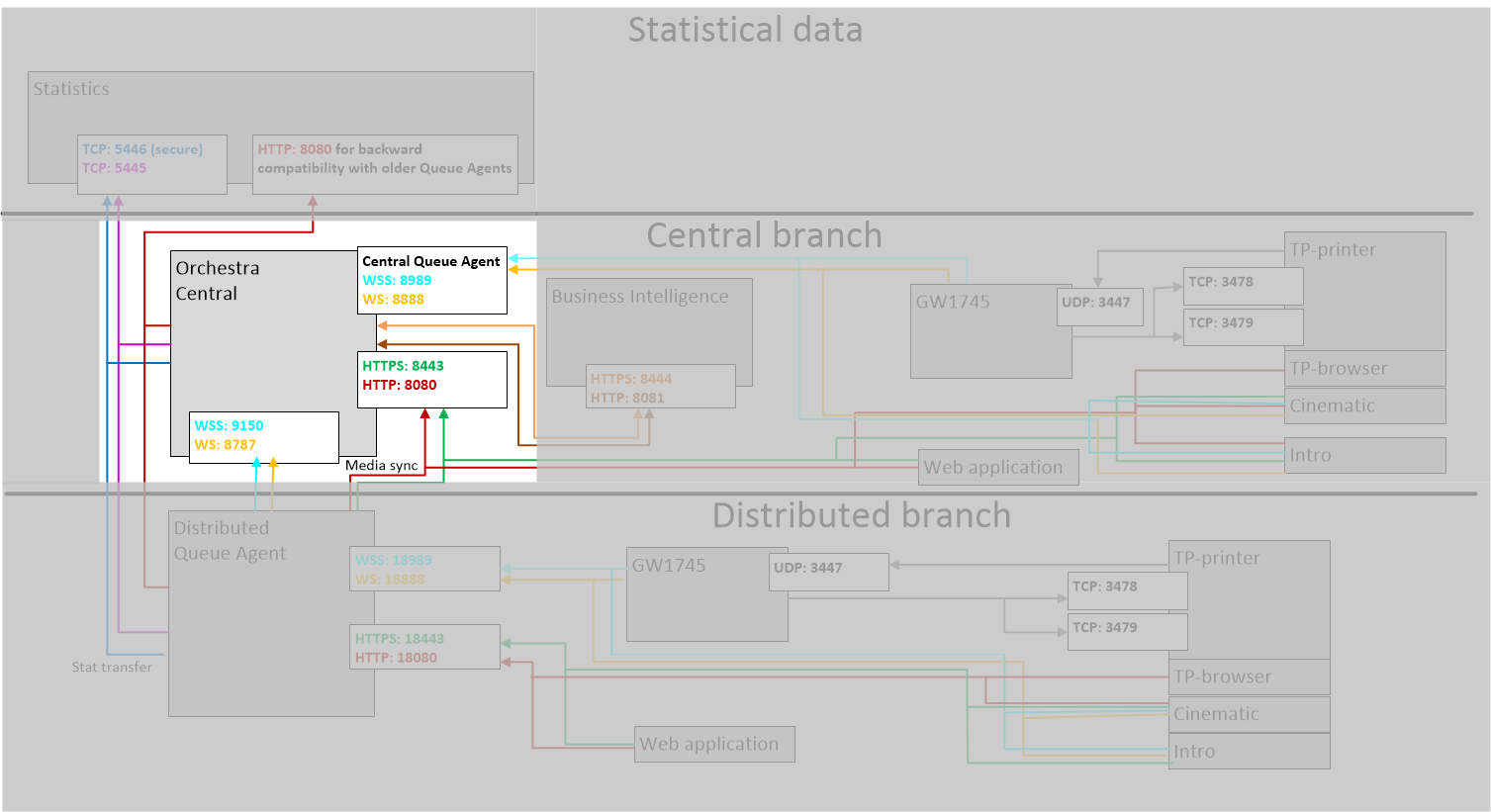
In this first scenario, we will secure the communication for Orchestra Central, highlighted in the following picture:
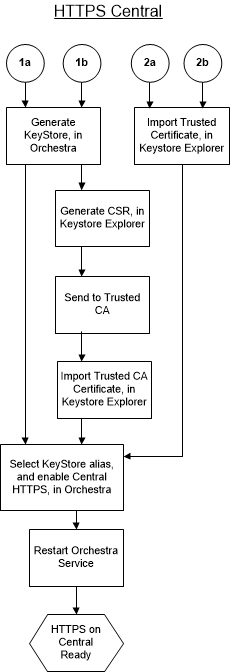
The following flow chart illustrates the steps that need to be taken to set up HTTPS for Central. Each number (1a, etc) refers to a certificate type (see
See “Different kinds of certificates”.), described by a corresponding section below.
1a: Certificate Generated by Orchestra, used as is
1. First, a private key pair must be generated.
a) Navigate to the Parameters section of the System Administration application and locate the HTTPS Parameters section.
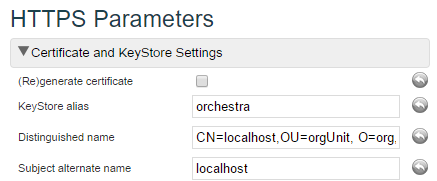
b) In the Certificate and key store Settings section, adjust the values below:
• KeyStore alias - The name of the certificate entry in the key store. This can normally be left as is (default: orchestra).
• Distinguished name - The distinguished name of the certificate. The "CN" part should be the host name of the Orchestra server, the other parts, i.e which organization, country etc need to be filled in, so they match the customer’s organization.
• Subject alternate name - This needs to be filled in, if the certificate should be valid for more than just one host name. For example, both host name and IP-address. Separate each entry with a comma.
Example: testrd.q-matic.net, 192.168.8.206
Once all settings have been set properly, Save the configuration.
2. Set the value for (Re)generate certificate to true and Save the configuration again.
This will generate a key entry in the keystore.

Do
not enable this setting once the HTTPS setup is complete, as it
will overwrite any certificate using the same alias in the key store, potentially destroying the HTTPS setup.
3. Navigate to the Parameters section of the System Administration application and locate the HTTPS Parameters section.
4. In the HTTPS server settings section, adjust the values below:
• HTTPS port - This is the port you want to use when running HTTPS, default is 8443.
• KeyStore alias - This should match the alias in the key store, used when creating / importing the alias, default is orchestra.
When both these settings are set correctly, set the value for HTTPS enabled to true and click Save.
This will enable HTTPS in the underlying server (Wildfly).
5. Next, restart the Orchestra service.
6. Test your https connection by entering the url https://<orchestra_ip>:<https port>, in your browser and making sure that everything works as expected.
1b: Certificate Generated by Orchestra, to be sent to a CA Authority
The certificate needs to be sent to a certificate authority to be properly signed.
Follow these steps:
1. In Keystore Explorer open the keystore. This should be the default keystore for Orchestra. This file is located in <installation directory>\conf\security and is called keystore.jks.
2. Right-click and select Generate CSR. The default password is changeit.
3. In the Generate CSR window, click Ok.
4. Send the certificate request (server-2048.csr) to your certificate authority (for example Verisign or Thawte).
5. Once the certificate response has been received, it must be imported into the keystore.
The certificate response normally consists of 3 parts:
• The certificate authority’s signer certificate, example: symantec-ca.cer
• The certificate authority’s root certificate, example: symantec-root.cer
• Your signed certificate, example: server-2048.cer
All these certificates must be imported into the keystore in the correct order (the one defined above).
Open Keystore Explorer and select Import Trusted Certificate, select the wanted files and import them.
Enter yes when prompted if the certificate(s) should be trusted.
6. Navigate to the Parameters section of the System Administration application and locate the HTTPS Parameters section.
7. In the HTTPS server settings section, adjust the values below:
• HTTPS port - This is the port you want to use when running HTTPS, default is 8443.
• KeyStore alias - This should match the alias in the key store, used when creating / importing the alias, default is orchestra.
When both these settings are set correctly, set the value for HTTPS enabled to true and click Save.
This will enable HTTPS in the underlying server (Wildfly).
8. Next, restart the Orchestra service.
9. Test your https connection by entering the url https://<orchestra_ip>:<https port>, in your browser and making sure that everything works as expected.
2a: Certificate Generated outside Orchestra, Signed / Created by Private CA Body
If your enterprise/company uses a certificate already created and signed by a Private Certificate Authority (CA) body, this certificate needs to be imported to your truststore, before you can use it.
1. Navigate to the Parameters section of the System Administration application and locate the HTTPS Parameters section.
2. In the HTTPS server settings section, adjust the values below:
• HTTPS port - This is the port you want to use when running HTTPS, default is 8443.
• KeyStore alias - This should match the alias in the key store, used when creating / importing the alias, default is orchestra.

Your private CA certificate should be available in this
drop-down.
When both these settings are set correctly, set the value for HTTPS enabled to true and click Save.
This will enable HTTPS in the underlying server (Wildfly).
3. Next, restart the Orchestra service.
4. Test your https connection by entering the url https://<orchestra_ip>:<https port>, in your browser and making sure that everything works as expected.
2b: Certificate Generated outside Orchestra, already signed by CA authority
If your enterprise/company uses an already signed Certificate Authority (CA) certificate, this certificate needs to be imported to your truststore, before you can use it.
Follow these steps:
1. In Keystore Explorer, select Open an exisiting KeyStore, browse for and open the keystore. which is located in <installation directory>\conf\security and is called keystore.jks. Enter the password for the keystore (the default password is changeit).
2. In the Tools menu, select Import Key Pair.
3. Select the wanted type of key pair, for example PKCS #12.

The format supported by Orchestra is pkcs12 files (i.e
*.p12 and
*.pfx files).
4. Specify the password for the certificate, then browse for and select the certificate file, and click Import.
5. Enter the Alias. This will be displayed in the Orchestra GUI.
6. Enter the Key Pair password. This must be the same as the password you entered in
1. Default is
changeit.
7. Make sure that the key pair is imported correctly and save the updated keystore.
8. Navigate to the Parameters section of the System Administration application and locate the HTTPS Parameters section.
9. In the HTTPS server settings section, adjust the values below:
• HTTPS port - This is the port you want to use when running HTTPS, default is 8443.
• KeyStore alias - This should match the alias specified in
5. Default is
orchestra.
 Your private CA certificate should be available in this
Your private CA certificate should be available in this drop-down.
When both these settings are set correctly, set the value for HTTPS enabled to true and click Save.
This will enable HTTPS in the underlying server (Wildfly).
10. Next, restart the Orchestra service.
11. Test your https connection by entering the url https://<orchestra_ip>:<https port>, in your browser and making sure that everything works as expected.

 Do not enable this setting once the HTTPS setup is complete, as it will overwrite any certificate using the same alias in the key store, potentially destroying the HTTPS setup.
Do not enable this setting once the HTTPS setup is complete, as it will overwrite any certificate using the same alias in the key store, potentially destroying the HTTPS setup.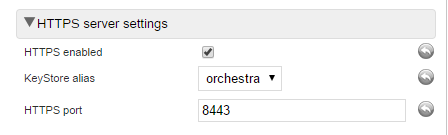


 Your private CA certificate should be available in this drop-down.
Your private CA certificate should be available in this drop-down. The format supported by Orchestra is pkcs12 files (i.e *.p12 and *.pfx files).
The format supported by Orchestra is pkcs12 files (i.e *.p12 and *.pfx files). 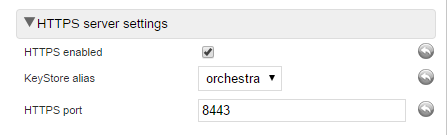
 Your private CA certificate should be available in this drop-down.
Your private CA certificate should be available in this drop-down.